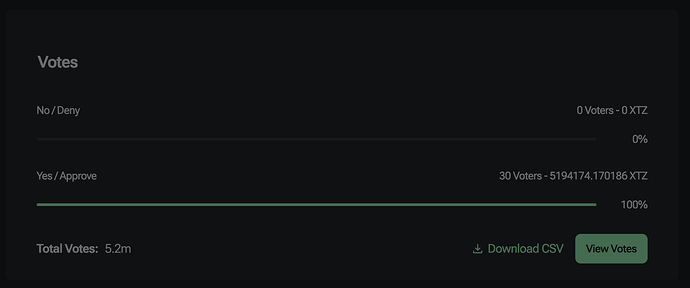
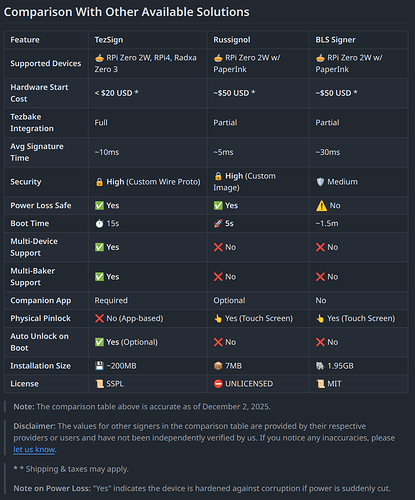
The Problem
Small to medium-sized Tezos bakers lack a dedicated, affordable, and secure hardware solution. They are forced to choose between:
- Complex software signers with a higher risk profile.
- Expensive, general-purpose hardware wallets that are not optimized for the unique demands of 24/7 baking.
With the advent of tz4 signature aggregating signing in the “T” protocol, small to medium-sized bakers no longer have the Ledger Nano line of products to use as their affordable hardware signers.
The upcoming Tezos “T” protocol will revolutionize key management with its 4-hour cooldown for consensus key switching. This opens the door for a new class of DIY, specialized, single-purpose signing devices like SBCs.
The Solution
TezSign!
We introduce TezSign: a dedicated, DIY Hardware Security Module (HSM) designed from the ground up to provide robust security through its specialized, single-purpose design for bakers, at a hardware cost under $20.
It is a single-purpose “baker companion” that does one thing perfectly: it signs baking operations securely and rejects everything else.
 Simple, Focused, and Accessible
Simple, Focused, and Accessible
Plug-and-Play Security: A headless, low-power device. It’s USB-powered and managed by a simple utility app on the baker’s machine, ensuring a minimal footprint and effortless setup.
 Radically Affordable:
Radically Affordable:
By leveraging inexpensive and widely available Single-Board Computers (SBCs), we make cheap, robust security accessible to every baker.
Sample target devices: RADXA ZERO 3W and RPI ZERO 2W
 Uncompromising, Purpose-Built Security
Uncompromising, Purpose-Built Security
Baking Operations Only: TezSign is hard-coded to sign only blocks and attestations. It will categorically deny any other transaction request (e.g., fund transfers), completely eliminating the risk of a compromised baker machine draining your wallet.
 Future-Proof Cryptography:
Future-Proof Cryptography:
To conform with the latest developments of the Tezos protocol, we will provide BLS-only signatures.
 A New Paradigm: Resilience Over Recovery
A New Paradigm: Resilience Over Recovery
Designed for Protocol T: Our “no recovery” philosophy aligns perfectly with the new protocol. Keys are generated on-device and are not meant to be backed up with a seed phrase, making TezSign the ideal consensus/companion device.
 Eliminates Catastrophic Penalties:
Eliminates Catastrophic Penalties:
If a baker wants to move to another device while the old one is still in use, instead of restoring a backup, they simply generate new keys on the new hardware. This workflow eliminates the risk of double-baking or double-attestation.
 Multi-key Baking:
Multi-key Baking:
A baker can load his or her consensus and companion keys on the same TezSign SBC. It’s possible to run multiple bakers on the baker machine with multiple consensus and companion keys.
How does this product work in practice?
- A baker purchases an SBC for under $30 along with an SD card
- Baker burns in SD card
- Baker connects SBC via USB to baking machine
- Baker runs
tezsign new-key bakeron the baking machine - Baker is ready to attest blocks
What happens if the baker needs to shut down baker?
The baker boots up the baker, plugs in the SBC and runs tezsign unlock ...
What happens if the TezSign SBC is stolen?
The attacker obtains encrypted version of baker’s consensus private key. The baker rotates consensus keys and continues to bake safely.
Community & Go-to-Market
Strategic Go-to-Market: Our goal is to have TezSign ready for the deployment of the “T” protocol.
 Tinkerer-Friendly Foundation:
Tinkerer-Friendly Foundation:
The core software is written in highly-optimized Go, making the code base transparent, easy to audit, and welcoming for community developers to build upon, customize or even fork.
The Ask & Funding Strategy
We are seeking funding to accelerate the core development, testing, and preparation for a community launch. We ask for 20,000 XTZ to deliver a fully working product, ready to use in production.
This initial funding is designed to kickstart the project and reach key milestones, making it production ready but not fully feature rich, yet. We anticipate it will be subsidized by TzC donations and other funds as needed to carry the project through to a fully-realized feature set.
Team Information
Name: Primate & V from Tez Capital
Email or contact method: .primate & .v_alis.is on Discord
Geographic location: Florida, USA
Are you applying on behalf of a company, or as an individual:
If company, provide company name and website: GrokTech LLC https://groktech.xyz
Name of project or idea: TezSign
Detailed description of your project or idea and why you believe it deserves funding: (included above)
What type of background or experience do you have and your team have in building out a project like this: We have been building in the Tezos ecosystem since 2021. Our products include: TezBake, TezPay, TezGov, TezPeak, TezWatch and Starlords.app
Social handles of project, if any: https://x.com/TezCapital/
Funding amount being requested (please make sure the DAO treasury can currently support it, suggested range is 500–20,000 tez depending on project requirements and value):
Tez address to be funded (please verify accuracy): 20,000 @ tz1aLN3iQ9SYex3tdUuvUwcb6DJYR8F9yMLP
Proposed goals/GPIs to deliver for the requested funding (funding may be broken into two tranches, with final half distributed after some proven deliverables):
Parting words…
Cutting off Ledger baking access in future proposals, once only tz4 is usable, has the potential to knock off many small and medium bakers, lowering our validator numbers and removing the accessible baking mantle from the blockchain.
We believe that having multiple cheap hardware signers ready for the “T” protocol, to use with TezBake or directly with Octez, gives us the best chance of retaining the most small and medium bakers.